ISIS Hacks Into French Television
Thursday, April 9th, 2015April 9, 2015
The terrorist organization Islamic State (ISIS or IS) hacked into France’s television network TV5Monde, beginning last night at about 10 pm (all times given are Paris time). The hackers (people who “break into” computers or systems by defeating electronic security measures) were able to black out all 11 of the broadcaster’s television channels, its websites, and its Facebook page. TV5Monde is a public-service network founded by the French government in 1984. The French government called the hacking an act of terrorism.
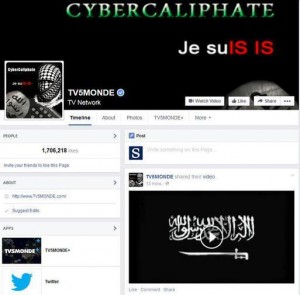
This screenshot, provided by TV5Monde on Thursday, April 9, 2015, shows it’s Facebook page after hackers claiming allegiance to the Islamic State group accessed the site. (Credit: TV5Monde)
Once the illegal access to the network began, viewers saw a black screen with the phrases “Cybercaliphate” and “Je suis IS” (the latter meaning I am IS). To explain these phrases, in 2014, the leader of ISIS, Abu Bakr al-Baghdadi, after gaining control of land in Syria and Iraq, proclaimed himself caliph over those lands. A caliph is a leader with political and religious authority whom Muslims recognize as a successor of the Prophet Muhammad, and his government is a caliphate. “Je suis ISIS” refers to the phrase “Je suis Charlie,” which was used worldwide as a reaction of solidarity with the staff of the magazine Charlie Hebdo. Eleven people were killed when the magazine’s staff was attacked by Islamic terrorists in January 2015. The hackers also posted messages warning French soldiers to “stay away from the Islamic State.” France is part of a United States-led coalition carrying out air strikes against Islamic State targets.
By 10 am today, TV5Monde had regained control over its networks, although initially, only to broadcast pre-recorded material. The network was able to broadcast live programming by around 6 pm today. The hacking represents a much more sophisticated cyber crime than ISIS has been capable of in the past. The French minister of culture, Fleur Pellerin, called a meeting of all major newspapers, television networks, and the news service Agence France-Presse to discuss security measures.
Other World Book articles:



